Congressional Hackathon 7.0: Coding, Collaboration, and Culture Change on Constitution Day
Meanwhile, Congress debates its own security while members negotiate over whether and how to push back on Trump's incursion on Congressional powers
The Congressional Hackathon that took place this past Constitution Day is a rarity in today's Washington. Civic minded citizens joined with congressional staff in a day-long discussion inside the U.S. Capitol on strengthening Congress by improving and democratizing its technology.
The bipartisan nature of these events is a recurring theme, with senior Republicans and Democrats always offering opening remarks and providing space and support inside Congress. Indeed, the Speaker broke news at the Hackathon, announcing the House would be distributing up to 6,000 user licenses to congressional staff to use Microsoft’s M365 Copilot AI-powered chatbot for a year.
This is the seventh such Congressional Hackathon, with the first organized back in 2011. This iteration also was the fourth annual event in a row. I've been to them all and this event brought forth a groundswell of energy. Some of it came from the new coding breakout session, where almost 90 participants built tools side-by-side with congressional staff that provide insight and services to people in Congress, across government, and around the country. It reminded me of the civil society-organized hackathons of the 2010s that had so much energy and potential. We all owe a debt of appreciation to Speaker Johnson, Democratic Leader Jeffries, and CAO Catherine Szpindor for co-hosting.
Collaboration and culture change
One thing that has changed over the last fifteen years is the nature of congressional-public collaboration. In the beginning, some inside the congressional firmament were opposed to releasing data to the public. Even using the word "hack," as in hackathon, was controversial. It took bipartisan leadership from Reps. Boehner, Cantor, McCarthy, Hoyer, Honda, Issa, and many others (including many unsung staff in political and non-political offices) to bend the arc. Now there is a culture shift, where many in the Legislative branch embrace modernization and the pockets of resistance have grown smaller and less influential.
Since the Hackathon became an annual event in 2022, presenters in its “lightning round” phase have steadily demonstrated more and more new projects and tools utilizing increasingly accessible legislative data. The origins of the culture change in Congress were a fight over whether data about legislation should be made publicly available. The result wasn't just the publication of bulk access to legislative data, but the creation of the Bulk Data Task Force, a like-minded group of internal and external stakeholders that has been meeting quarterly for 13 years, encouraging and supporting technological modernization. One outcome was the Library's granting of a longstanding public request for publication of congress.gov data as an API, which launched in October 2022. That API, its manager announced, has received 1.3 billion requests over its three year existence.
The Hacking Session
Last week, the progress made in bringing Congress into the digital age allowed developers for the first time to work on projects collaboratively during a morning session of the Hackathon. Some participants utilized a nascent Legislative branch data map, the existence of which had been requested by Appropriators. The map is an effort to identify across the Legislative branch the different sources for congressional data and drew rhetorical inspiration from the 2013 executive order on making open and machine readable the new default for government information, the 2018 Open Government Data Act, and advocacy from public-interest minded groups.
The map data was seeded from my 2023 biased yet reliable guide to sources of information and data about congress and collaborations from governmental members of the Congressional Data Task Force, although its GitHub repository quickly drew pull requests from hackathon participants as well. In other words, anyone can suggest items to add to the list of Legislative branch data sources and that list can point to official and non-official sources for data. This is important because it's very hard to find data about Congress and a lot of the data is published in ways that are hard to reuse.
The map improves the findability of information and makes it discoverable when someone has done the hard work to refine that information into a useful format. It was my pleasure to present, along with the House Digital Service's Steve Dwyer, on this new map that will catalyze the ability of technologists to build tools for and about Congress.
The data map became immediately handy during the coding portion of the hackathon, where Steve and I highlighted it to the coders who were present in the side room. Among the hacking projects presented at the end of the day were:
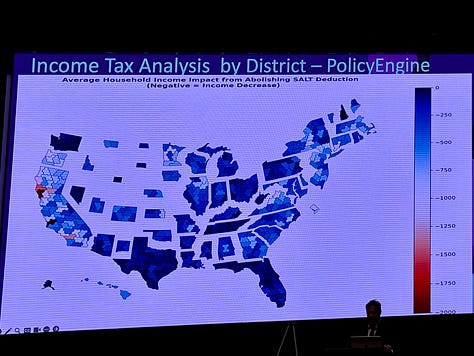
Income tax analysis by congressional district, looking at the changes in taxation resulting from abolishing the SALT deduction, from Policy Engine. (Click through to see the visualizations.)
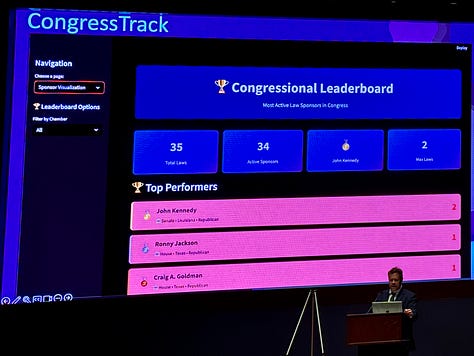
CongressTrack, an effort to show the extent to which politicians keep their campaign promises.
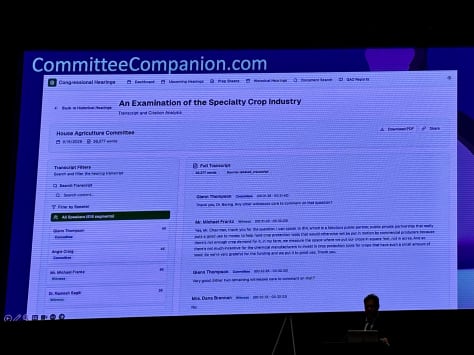
Committee Companion, which uses AI to generate well-formatted transcripts from committee proceedings.
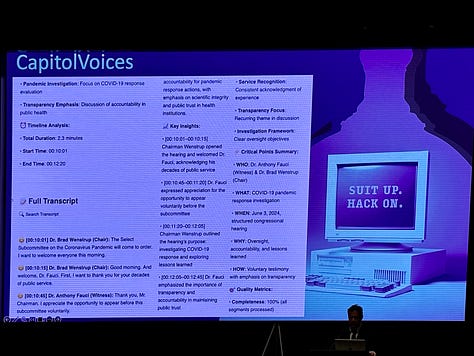
Capitol Voices, which creates AI-powered congressional hearing transcription and analysis. It also identifies the speakers, themes, and sentiment analysis.
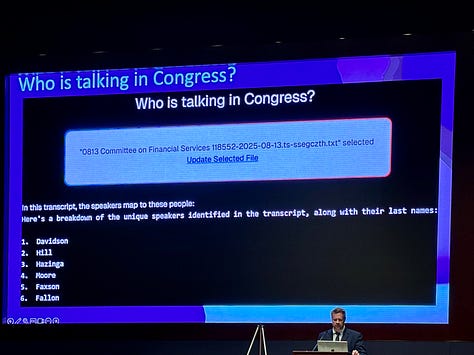
Who is Talking in Congress, which breaks down the unique speakers identified in a transcript and their last names.
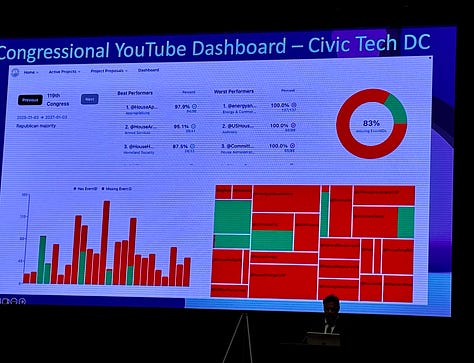
Congressional YouTube Dashboard, a Civic Tech DC congressional-tech project that identifies how often House committees remember to publish the event IDs in YouTube videos. It is only through these event IDs that the Library of Congress identifies that a particular YouTube video is associated with a particular hearing. Notably, this project shows which committees are good at adding these IDs and which ones are lagging. Click through this link to see the visualization of the best and worst performing committees.
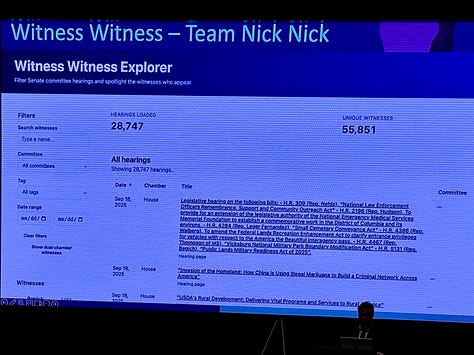
Witness Witness, a proof of concept that creates a central tracker for all House and Senate hearing witnesses. They identified more than 55,000 unique congressional witnesses across 28,000 hearings. They wrote about their efforts on LinkedIn and posted this live demonstration. (Note: be patient while it loads… it's worth it.)
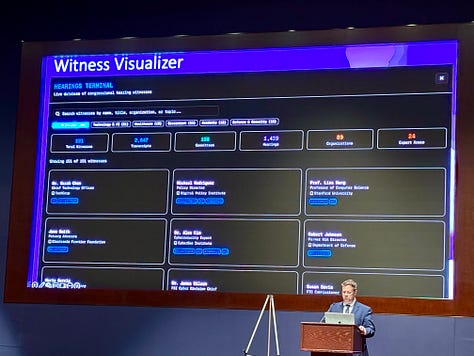
Witness Visualizer, which creates an interactive knowledge graph visualizing the relationships between (House) witnesses, committees, topics, and organizations.
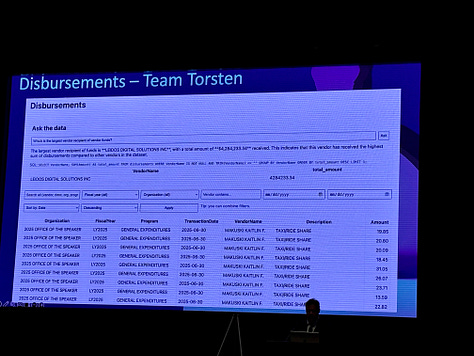
Disbursements, which moves House Disbursement (i.e. spending) data into a database and provides the ability to search and filter the data as well as for users to ask questions (via AI) concerning the dataset.
Additional projects. A few presentations during the lightning round also have great relevance to the development of technology tools and we want to highlight them here.
Hearings, presented by Abigail Haddad, is a great project that uses logic to identify the relevant YouTube video for a House hearing even when the committee has failed to include an event identifier. The live demo, focused on the House Energy and Commerce Committee, shows where the developer was able to match a hearing name with the correct YouTube video.
Craig Butler from the House Digital Service and Pat O'Brien from the Senate Democratic Steering and Policy Committee demonstrated an extension of the old Capitol Bells App to digitize the old clock alert system in buildings on the congressional campus. This new system retrofits congressional clocks to transmit a digital signal when vote alarms sound, pushing out notifications and creating new entries in HouseCal.
Bill Tracer, developed by Ruzanna Gaboyan and Philip Golczak, creates a track-changes comparison between the introduced and engrossed versions of a bill, with a particular focus on appropriations bills. (The House has built its own comparative print tool, but it's not available to the public. GovTrack.us has a version of this, and Bill Tracer is working off GovTrack data.)
We already mentioned the presentation from the Library of Congress's Andrew Weber on the Congress.gov API, but we would be remiss not to mention that the API now has some CRS reports and House Roll Call votes. If you want new features for the API, a great place to request those features are on the Library's GitHub repository, through the Library's survey form, at the quarterly Congressional Data Task Force meetings, and at the Congress.gov public forum on September 30th.
Other presentations during the lightning round of the afternoon’s session demonstrated the innovative potential in using large language models and machine learning with the data available through the congres.gov API. Two projects, including one developed by a pair of Fairfax County high school students, addressed accessibility issues with government publications for people with disabilities. The nonprofit Policy Engine introduced their system that extrapolated the economic impact of bills onto the state and district level.
Digging into what happened at the break-out groups would make this already-long article unwieldy. Don't worry – we will write up the Congressional Hackathon 7.0 on the Congressional Data Coalition blog, just as we have written up hackathons 1-6.
Finally, if you want to stay up to date on what's happening with Congressional data, reach out and let us know. (Just reply to this email.) We have coordinated the Congressional Data Coalition since its inception more than a dozen years ago and I occasionally send out announcements about upcoming events and opportunities to engage with Congress.
Daniel Schuman
POWER OF THE PURSE
The House approved its clean CR Friday and then left town without plans to be back in session until after the end of the fiscal year. After the Senate declined to adopt a CR on a rare Friday vote, Democratic congressional leadership reached out to President Trump in search of a new pathway forward in negotiations to avoid a shutdown.
Friday, the Senate rejected Democrats’ month-long CR proposal that included some provisions to protect the congressional power of the purse, as Daniel suggested they include to The American Prospect’s David Dayen last week. The Democrats’ version extended the availability of funds targeted for “pocket rescissions” by the Trump Administration, including for the NIH. It also eliminated the “fast-track” procedures for rescissions under the Impoundment Control Act that allow approval via a simple majority in the Senate, which threatened to reverse any spending deal the Democratic minority would make. That proposal also would prevent the White House from sending rescission messages in the final 90 days of a fiscal year. It also prohibited reducing program funding within the FY 2026 budget during the span of the CR. The Democratic version also established an inspector general office inside OMB, an idea that also has the support of House Appropriations ranking member Rosa DeLauro.
Senate Democrats also remain committed to restoring health care subsidies and funding cuts that amount to around $67 billion a year, which is a much bigger political issue. Nevertheless, they have established a position that this White House cannot be trusted to enact appropriations agreements negotiated in Congress. Here, they have common ground with several senators across the aisle who recognize the Administration has, through impoundments and drastic reorganization of federal agencies, made the conventional appropriations process effectively impossible. Compromise on measures restoring some congressional control over spending would be a win for the institution in this showdown.
Rep. DeLauro raised how the pocket rescission issue was disrupting the appropriations process in the amicus brief she filed on September 12 to the Supreme Court for Department of State v. AIDS Vaccine Advocacy Coalition. Appropriations negotiations, she noted “require stability and predictability in the executive branch’s execution of laws making appropriations.” The court “affording any credibility to the government’s argument that the President can unilaterally rescind appropriations without congressional approval,” which she notes was “soundly rejected” by Senate Appropriations Committee Chair Susan Collins, “threatens to disrupt this process.”
The Center for Budget and Policy Priorities has estimated that $26 billion in funds approved last March is at risk of expiring on September 30 based on slower-than-expected spending projections from July. Its report last week identified 25 accounts that were 20 percentage points behind typical obligations rates through July, including those targeted for elimination by the Administration like minority business development aid and foreign aid. Delays also affected programs at NIH and the Centers for Disease Control and Prevention.
“If a 2026 funding bill doesn’t have enforceable provisions that take on impoundment and rescission,” CBPP concludes, “the Administration could be emboldened to impound more funds from more accounts in the future, using its 2026 budget request as a guide.”
The House, meanwhile, continues to accept Executive branch usurpation of its taxation power on tariffs. Only Reps. Thomas Massie and Don Bacon voted against a motion to table a resolution instructing the Trump Administration to end tariffs on Brazil last Tuesday. Bacon asserted on X/Twitter, “Article One of the Constitution gives Congress the authority to determine tariffs.”
Chris Nehls
MEMBER SECURITY
The House CR isn’t precisely “clean” as it approved $30 million in additional funds for mutual aid agreements between the Capitol Police and state and local departments as security concerns skyrocket. It also included $28 million for Supreme Court security and $30 million for the Executive branch. The Senate already approved a rules change last week to accept the $30 million for member security. (We note, parenthetically, that the Senate proposal would increase funds for member security at the expense of salaries for personal office staff, which is bad policy and creates bad incentives for senators. Security should be drawn from a separate account.)
The Democratic CR proposal would have gone further, proposing $66.5 million for enhanced member security programs at the Senate Sergeant at Arms and $140 million in added security for the judiciary.
Even if these funds help lead to more arrests, several Democratic members expressed doubt that the Justice Department will pursue prosecutions of those threatening them and their families. Rep. Eric Swalwell responded to a tweet by Attorney General Pam Bondi about threats of violence noting that her department had refused to prosecute multiple death threats targeting his family. Bondi subsequently called Swalwell about the matter. Rep. Julie Johnson told NOTUS she deeply doubted Bondi’s Justice Department actually would act because the president has “demanded strict, absolute, unconditional loyalty from the people he’s placed in offices to effectuate their jobs.” Just this weekend, Trump demanded Bondi prosecute his political enemies.
NOTUS also reported that Democrats had utilized the additional $5,000 a month allowed members to boost personal security at a rate of more than three-to-one compared to Republican counterparts.
Congressional security is a thorny issue and enactment of the Senate-approved Legislative Branch Appropriations bill would be a good way to start. We have long maintained that Congress needs to improve oversight and feedback mechanisms for the Capitol Police. This includes making the Inspector General fully independent and capable of reviewing the Capitol Police Board, providing the Board independent staff, requiring the Capitol Police to publish data on how substantiated threats are dealt with, hiring professional staff in the appropriations offices who are experts on law enforcement, transforming the police force into a protective force, and improving USCP transparency.
Congressional security must extend beyond the Capitol campus, however. Some programs provide increased security for members, such as funds for member home security systems and reviews of district office security. None of this will be sufficient to address threats arising from stochastic terrorism and it's likely that no amount of funds would ever be able to provide enough security to insulate against these types of threats. They arise in significant part from the confluence of unbalanced individuals, heated political accusations, and easy access to weapons. Congress has a role to play here if it chooses to do so.
Organized threats, by contract, can be addressed by the collaboration of the Capitol Police and the national security services to identify, arrest, prosecute, and convict those who make political threats against members of Congress and their staff. Confidence in such a system has been gravely undermined by the pardoning of the Trump insurrectionists and the weaponization of the Justice Department against Trump's political enemies. Should Congress choose to exercise its power of the purse, it could push to ensure that law enforcement enforces the rule of law. We discussed that in the previous section of the newsletter on the power of the purse.
We may be in the grips of a dangerous cycle where members of Congress who wish to oppose some Trumpist policies are afraid to do so because they fear the invective the president will aim in return will result in unwell or politically-motivated individuals doing harm to them or their families. That fear of speaking out makes the danger more potent, fueling a downward spiral. The only way out is courage – and a robust and well-trained congressional security apparatus supported by national law enforcement committed to the rule of law. Thus, the dilemma.
ODDS AND ENDS
The Office of the Whistleblower Ombuds is excited to announce its latest fact sheet on Tech Industry Whistleblowing. This resource outlines the whistleblower protections available to private sector tech workers who raise concerns about issues such as consumer safety risks. It also points readers to additional guidance and resources.
Repost POST. A large group of civil society organizations and individuals issued a letter last week to the General Services Administration to reinstate the API used to submit public comments on pending regulations, which GSA has disabled in August. Doing so, the groups assert, runs contrary to the intent of the Administrative Procedure Act.
Closed captioning pilot. Up to eight visitors to the House Gallery will have the opportunity to participate in a new pilot that provides real-time closed captioning for floor proceedings via tablet computers. The program was recommended by the Committee on House Administration Subcommittee on Modernization & Innovation, and additional tablets may be installed if needed.
Dodaro succession. Politico details the precarious situation of President Trump being charged with nominating a replacement for Comptroller General Gene Dodaro in December given GAO’s investigations of administration impoundments. Congress should change current law to insulate the Legislative branch office from Executive branch interference in its oversight mission.
New staff tech fellowship. Georgetown University’s McCourt School has launched a new Congressional Technology & Policy Fellowship for senior congressional staff. The six-week program is focused on equipping “legislative professionals with the insights to understand how technology can make or break the policies they develop every day, and how to approach legislation in a manner that positions it for successful implementation.” McCourt’s next information session for the program is September 26 at 5:00 PM. Fellows will receive a certificate of completion at the end of the program, which runs Friday evenings from late October through mid-December.
Democracy Awards. The Congressional Management Foundation has posted its ceremony for the 2025 Democracy Awards on its website in its entirety.

Daniel, Wow. I would love for bluesky friends to see progress behind the scenes many may not be aware of, but hesitate to share without permission. Gave them the link to subscribe but unsure how many have. They (We) share your goals, it's just a matter of interpretation how we get there. There's another from March they would really like to see too, probably more.
Also, is there a TechSpeak for old Dummies like me. API, etc. leaves me cold. I can think of quite a few bluesky tech-savvy followers who would also really appreciate seeing what you're doing.
So, okay to share or no?
Thanks!
Steve Sumner